AWS IAM
IAM Users & Groups
- Root account created by default, shouldn’t be used or shared, instead create IAM users
- Users are people within your organization, and can be grouped
- Groups only contain users, not other groups
- Users don’t have to belong to a group, and user can belong to multiple groups
IAM Permissions
- Users or Groups can be assigned JSON documents called policies
- These policies define the permissions of the users
- In AWS you apply the : don’t give more permissions than a user needs
Managed policies and inline policies
When you set the permissions for an identity in IAM, you must decide whether to use
- . Standalone policy created and administered by AWS.
- . Policy you create for specific use cases, and you can change or update them as often as you like.
- . Policy created for a single IAM identity (user, group, or role) that maintains a strict one-to-one relationship between a policy and an identity.
IAM Polices Structure
Consists of
- Version: policy language version, always include “2012-10-17”
- Id: an identifier for the policy (optional)
- Statement: one or more individual statements (required)
Statements consists of
- Sid: an identifier for the statement (optional)
- Effect: whether the statement allows or denies access(Allow, Deny)
- Principal: account/user/role to which this policy applied to
- Action: list of actions this policy allows or denies
- Resource: list of resources to which the actions applied to
- Condition: conditions for when this policy is in effect(optional)
The following example shows a resource-based policy that can be used instead of AWS JSON policy elements: NotPrincipal to explicitly deny all principals except for the ones specified in the Condition element. This policy should be added to an Amazon S3 bucket.
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "UsePrincipalArnInsteadOfNotPrincipalWithDeny",
"Effect": "Deny",
"Action": "s3:*",
"Principal": "*",
"Resource": [
"arn:aws:s3:::amzn-s3-demo-bucket/*",
"arn:aws:s3:::amzn-s3-demo-bucket"
],
"Condition": {
"ArnNotEquals": {
"aws:PrincipalArn": "arn:aws:iam::444455556666:user/user-name"
}
}
}
]
}IAM Password Policy
.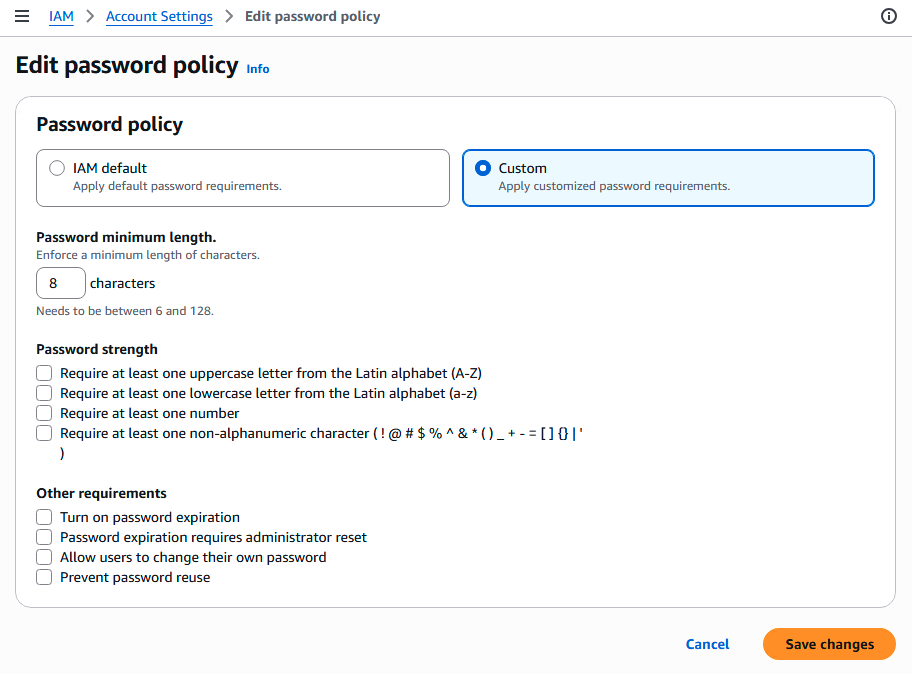
In AWS > IAM > Account settings, you can setup a password policy either or :
- Set a minimum password length
- Require specific character types: e.g. 1) including uppercase letters, 2) lowercase letters 3) numbers 4) non-alphanumeric characters
- Allow all IAM users to change their own passwords
- Require users to change their password after some time (password expiration)
- Prevent password re-use
Multi Factor Authentication - MFA
- Users have access to your account and can possibly change configurations or delete resources in your AWS account
- You want to protect your Root Accounts and IAM users
- MFA = password you know + security device you own
- Main benefit of MFA: if a password is stolen or hacked, the account is not compromised
The available MFA devices options in AWS:
- Virtual MFA device: Google Authenticator or Authy, phone only and support for multiple tokens on a single device.
- Universal 2nd Factor (U2F) Security Key: YubiKey by Yubico (3rd party), support for multiple root and IAM users using a single security key.
- Hardware Key Fob MFA Device: Provided by Gemalto (3rd party).
- Hardware Key Fob MFA Device for AWS GovCloud (US): Provided by SurePassID (3rd party).
Accessing AWS services
To access AWS, there have three options:
Access and manage Amazon Web Services through the AWS Management Console, a simple and intuitive user interface. You can also use the AWS Management Console Application to quickly view resources on the go.
The AWS Command Line Interface (AWS CLI) is a unified tool to manage your AWS services. With just one tool to download and configure, you can control multiple AWS services from the command line and automate them through scripts.
AWS CloudShell, which can be found next to the search bar in the AWS Management Console, provides a browser-based shell that is pre-authenticated with your console credentials. Using CloudShell, you can quickly run AWS commands and scripts without leaving your web browser.
Our Software Development Kits (SDKs) simplify using AWS services in your applications with an Application Program Interface (API) tailored to your programming language or platform. The AWS CLI is built on the AWS SDK for Python(Boto3).
Access keys are generated through the AWS Console. Users are responsible for managing their own access keys and should avoid sharing them. The Access Key ID functions like a username, while the Secret Access Key functions like a password.